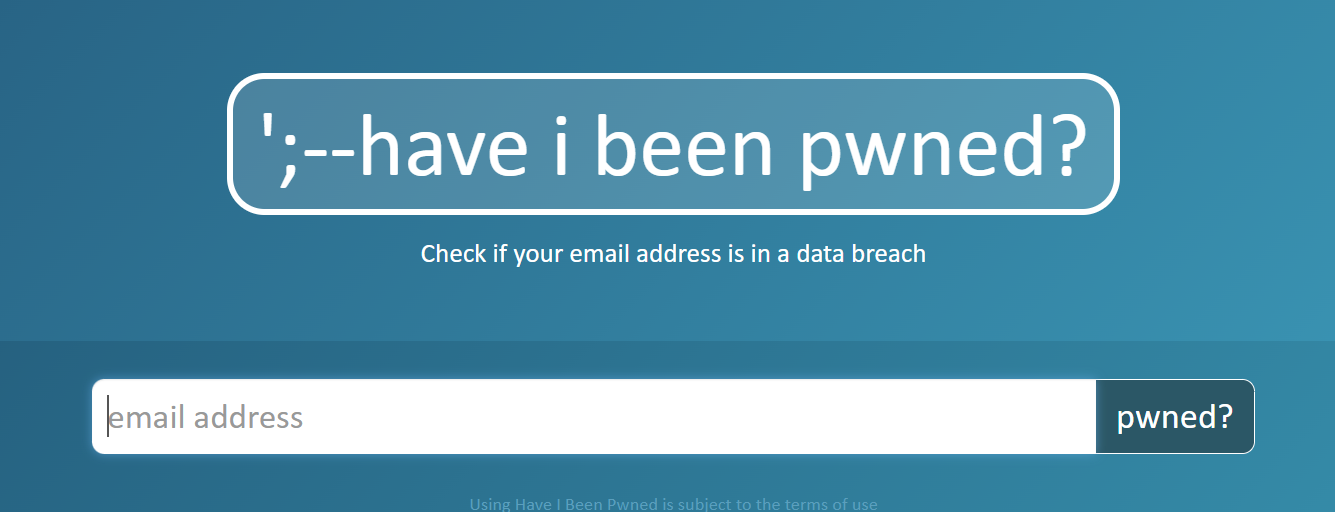
Have I Been Pwned (often abbreviated as HIBP) is a free online service that allows users to check if their personal data, such as email addresses or usernames, has been compromised in data breaches. Created by Australian security expert Troy Hunt, the platform aims to increase awareness about cybersecurity risks and help individuals take necessary precautions to protect their online accounts.
Visit www.haveibeenpwned.com
Key Details About Have I Been Pwned:
- Overview:
- Launched: December 2013.
- Founder: Troy Hunt, a prominent cybersecurity expert and Microsoft Regional Director.
- Purpose: To provide a simple way for individuals to find out if their personal information has been exposed in data breaches.
- Core Features:
- Email/Username Search:
- Users can enter their email address or username to check if it appears in any publicly known data breaches.
- Password Search:
- A separate tool, called “Pwned Passwords,” allows users to check if a password they use has been exposed in breaches.
- Passwords are hashed for privacy and security during the search process.
- Notifications:
- Users can sign up to receive alerts if their email address is found in future breaches.
- Data Breach Database:
- Includes information from thousands of breaches, with billions of compromised accounts indexed.
- Email/Username Search:
- Privacy and Security:
- No Password Storage:
- The site does not store passwords entered by users; instead, it uses a hashed comparison system to maintain security.
- Secure Searches:
- All searches are conducted privately, and user data is not shared or logged.
- Partnerships:
- Trusted by organizations and governments for its integrity and reliability.
- No Password Storage:
- Popular Use Cases:
- For Individuals:
- Check if your accounts have been compromised.
- Learn which breaches exposed your data and take action, such as changing passwords.
- For Organizations:
- Companies can integrate HIBP into their systems to monitor employee email accounts for breaches.
- For Security Professionals:
- Used as a tool to educate users about cybersecurity risks.
- For Individuals:
- Database Scale:
- As of recent updates, HIBP indexes over 14 billion breached accounts from thousands of data breaches, making it one of the largest repositories of breached data.
- Notable Features:
- Pwned Passwords:
- Offers an API for developers and businesses to integrate password security checks into their systems.
- Breach Details:
- Provides detailed information about each breach, including the type of data exposed (e.g., passwords, email addresses, credit card numbers).
- Open Source:
- Parts of HIBP, including the Pwned Passwords service, have been made open source to enhance transparency and community collaboration.
- Pwned Passwords:
- Strengths:
- Free to Use:
- Basic email and password checks are free for all users.
- Ease of Use:
- Simple and intuitive interface for checking exposure.
- Trusted Source:
- Recognized as a credible and widely-used tool in the cybersecurity community.
- Free to Use:
- Challenges and Criticism:
- False Sense of Security:
- Users should note that not all breaches are included in the database, so a “clean” result doesn’t guarantee complete safety.
- Focus on Public Data:
- HIBP only includes breaches that are publicly disclosed, which means some private or undisclosed breaches may not be indexed.
- False Sense of Security:
- Competitors/Alternatives:
- DeHashed: Provides broader search capabilities, including phone numbers and IP addresses.
- Firefox Monitor: Uses HIBP’s database to alert users of compromised accounts.
- Cybernews Personal Data Leak Checker: Offers similar email breach checking services.
- How to Use It:
- Visit www.haveibeenpwned.com.
- Enter your email address or username in the search bar.
- Review the results to see which breaches (if any) your data is part of.
- Take appropriate actions, such as changing passwords or enabling two-factor authentication.
Summary:
Have I Been Pwned is an essential tool for anyone looking to improve their online security. By providing insights into compromised accounts and breached data, it empowers users to take proactive measures to protect themselves. Its transparency, simplicity, and credibility have made it a go-to resource for both individuals and organizations concerned about data breaches.
Visit www.haveibeenpwned.com to check if your information has been exposed and learn how to secure your accounts!